黑盾杯2022线上writeup
Do you secure
dirsearch扫到upload.php
条件竞争
1 | import requests |
dirsearch扫到upload.php
条件竞争
1 | import requests |
某天准备用自己抓包写的脚本爬一些fofa上的数据时,发现出错了
1 | { |
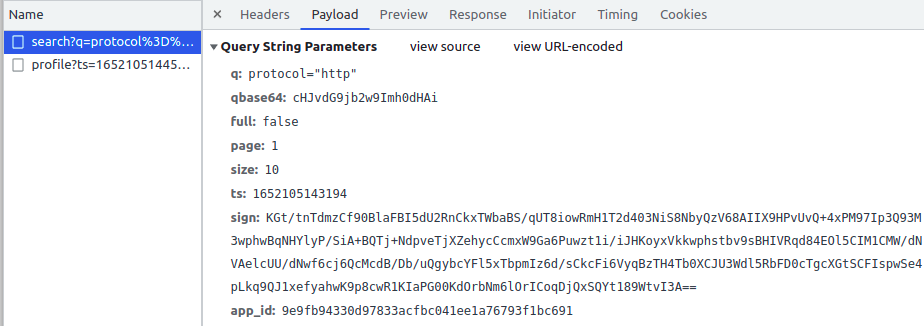
经过抓包,发现请求多了ts sign app_id 三个参数,关键是sign
使用checksec检查保护
1 | checksec rop |
丢进IDA查看源码
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
Nya~